¶ Introduction
This document describes how to configure Microsoft Azure to support SAML SSO with the Wyebot cloud dashboard. These instructions were written using the Azure Admin Console in August 2022.
The Wyebot cloud dashboard supports IdP-initiated SAML SSO. This means the browser session starts at the IdP where the user logs in - not at the Wyebot cloud dashboard. After a successful authentication, the user’s browser session is redirected to the Wyebot dashboard where the session is validated and the user is granted access. The main benefit of SAML SSO is that user credentials are only stored locally in an organization’s infrastructure.
All SAML users are treated as Administrators on the Wyebot dashboard. Limited users are currently not supported for SAML authentication.
On the Wyebot dashboard, user types of Admin and Limited are considered Local users. Password information for these users is stored locally in the Wyebot cloud database. SAML users are Non-Local users and no password information is stored locally for them.
You must always have at least one Local user configured on the dashboard. If your organization wishes to exclusively use SAML users, simply keep one Local user account configured on the dashboard. A Local user can have the same username as a SAML user.
¶ Terms Used in This Document
SAML - Security Assertion Markup Language is a standardized method of authenticating and redirecting browser sessions.
SSO - Single Sign-On allows a user to log into one site and reuse credentials across multiple other sites.
Identity Provider (IdP) - The device or provider that performs the authentication. In this example, the authentication is done by Active Directory.
Service Provider (SP) - The service that a user wishes to use. In this example, the SP is the Wyebot cloud dashboard.
SAML User - The user that is attempting to authenticate and access the SP. The user’s credentials are not stored on the SP, only on the IdP.
Consumer URL - The URL an IdP forwards a SAML request to following a successful authentication.
¶ Overview of Steps
The following steps must be completed to allow SAML SSO with the Wyebot dashboard:
- Create the SAML App on the Azure Admin Console.
- Enable SAML support on the Wyebot dashboard and configure IdP information.
- Complete the setup on the Azure Admin Console.
Add AD users from the Azure Admin Console.
¶ Add Custom SAML App on the Azure Admin Console
This step requires a Microsoft Azure account with Administrative privileges.
Log into the Admin Console at https://portal.azure.com. Click on Microsoft Entra ID from the Azure Services page.
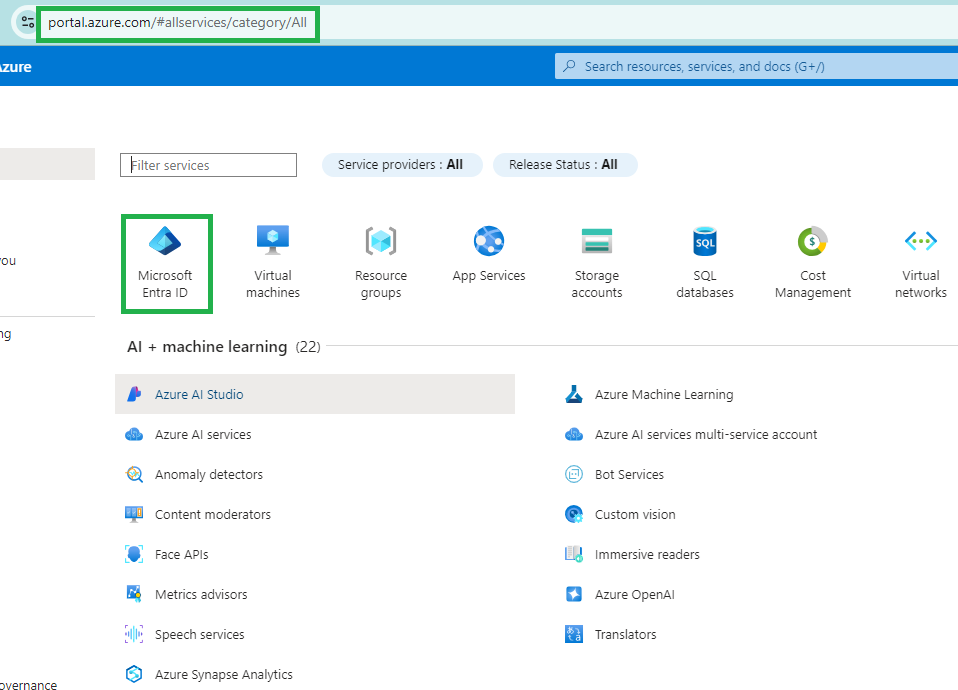
From the Add menu, select Enterprise Application.
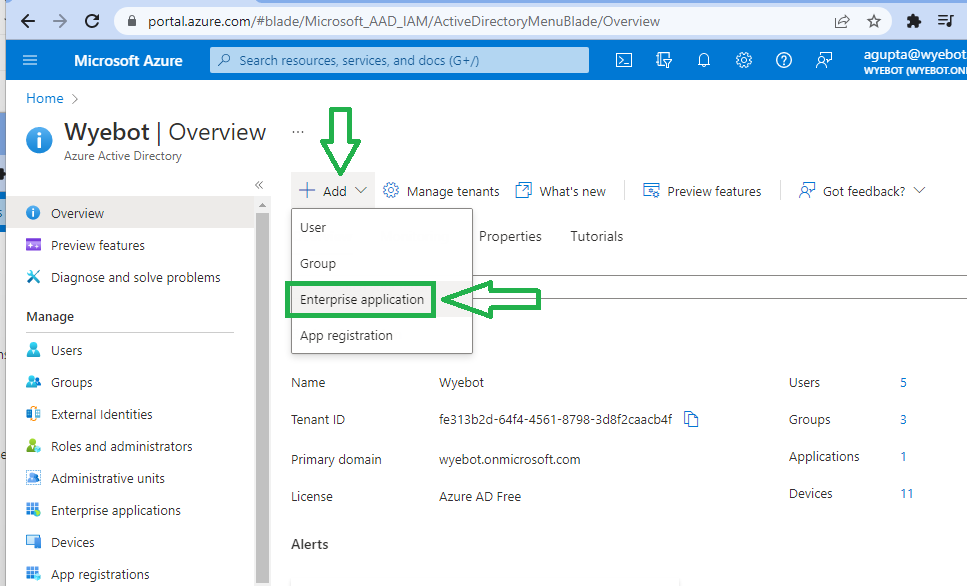
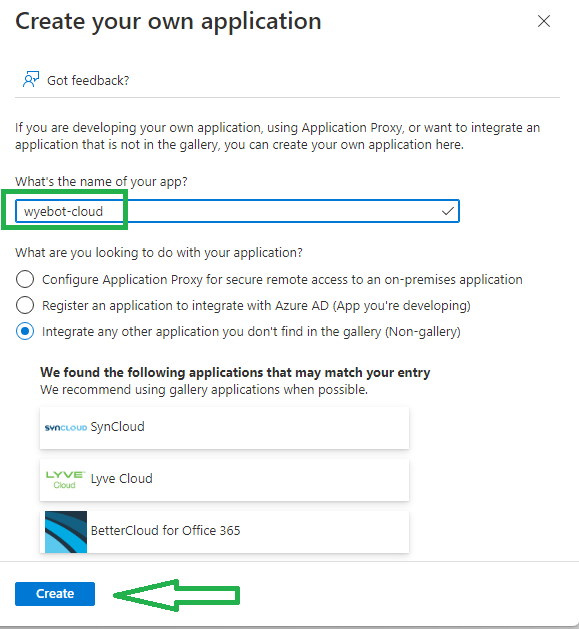
Click Create Your Own Application on the AD Gallery page.

Give a name for the application. In this example, it is called wyebot-cloud. Select the Non-gallery radio button and click Create.
Select Single Sign-On from the left menu and click SAML.
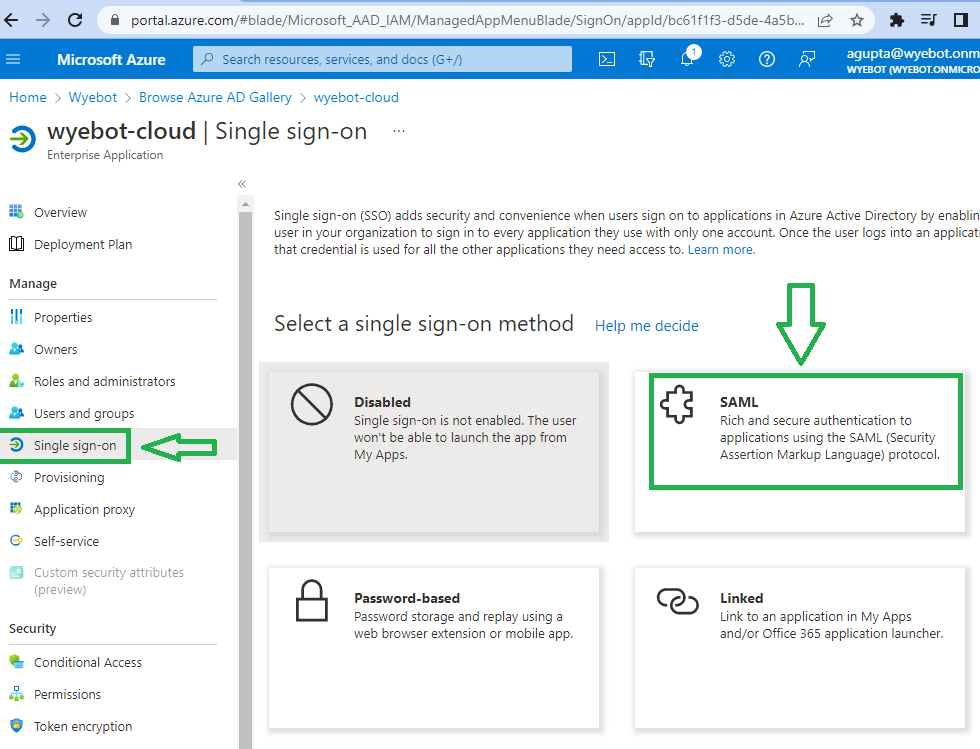
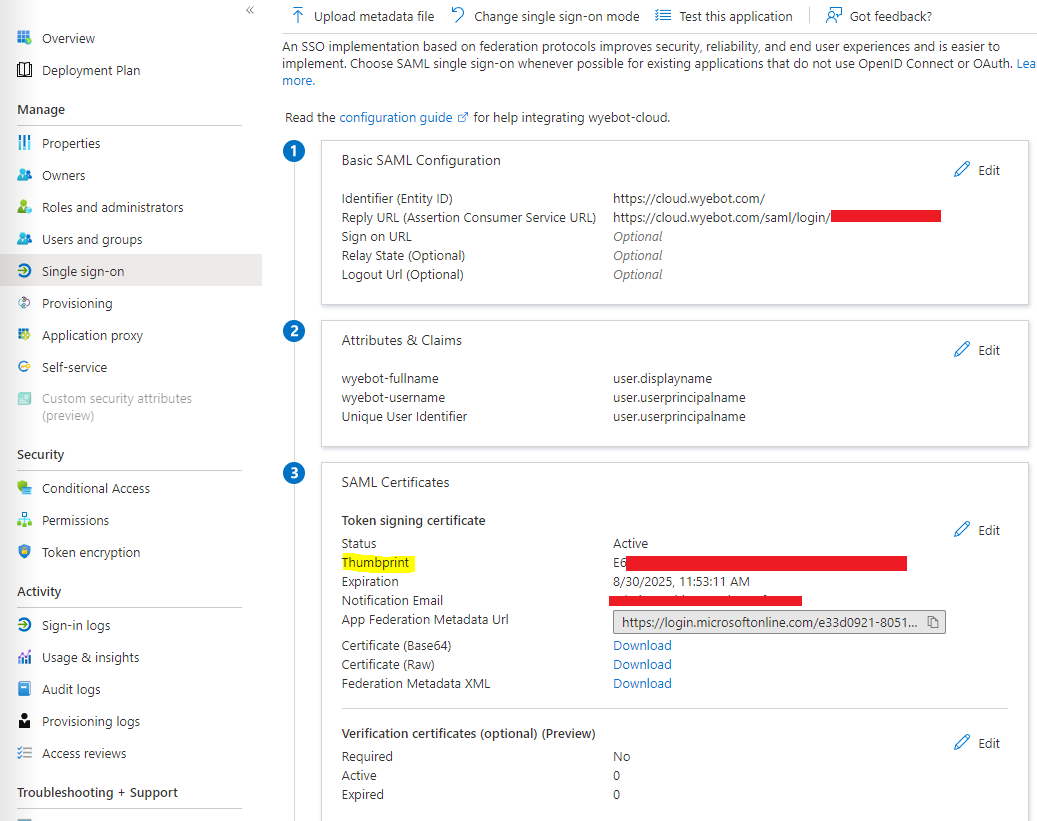
Copy the SAML Signing Certificate Thumbprint for use in the next step. You will now need to create an IdP profile on the Wyebot dashboard in order to get the dynamic Consumer URL used in the next step of configuring the Azure App.
¶ Configure SAML Support on the Wyebot Dashboard
In a separate browser tab, login to your Wyebot Dashboard and navigate to the Management → Users tab. Select the Enable radio button next to SAML Authentication. Click Add IdP. In the new window provide the following information:
IdP Name: a name to identify this IdP
SHA Fingerprint: the 32-byte fingerprint from the IdP certificate (saved from the previous section) Paste Thumbprint copied from Azure Console here.
Logout URL: this field is optional and can be used to redirect the user’s browser after logging out of the Wyebot dashboard.
Consumer URL: dynamic URL that is generated after creating the IdP profile
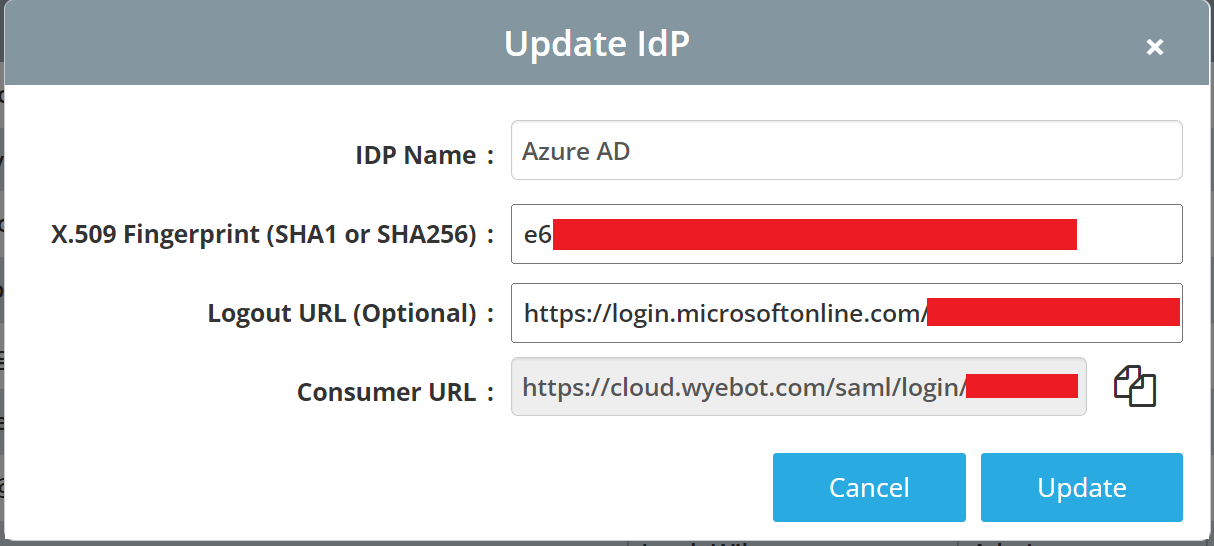
After creating the IdP profile, copy the Consumer URL that was generated. This will be required to complete the Azure configuration in the next step.
¶ Complete Azure App Configuration
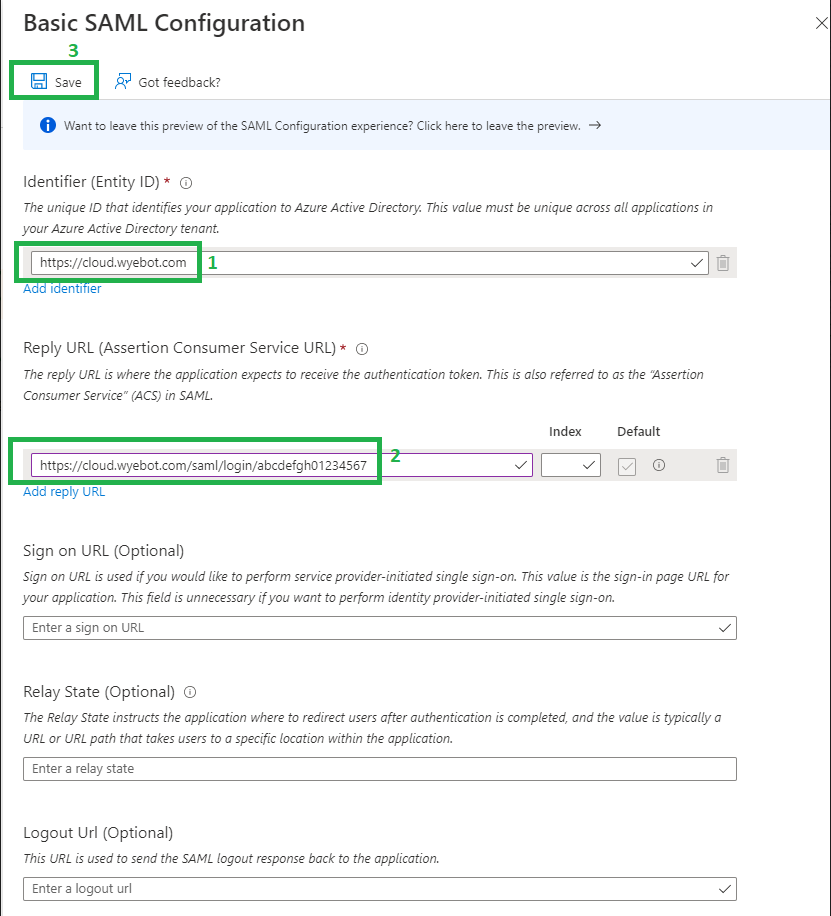
Go back to the Azure Admin Console browser tab. Edit Basic SAML Configuration.
Under Identifier, click Add identifier and paste https://cloud.wyebot.com.
Under Reply URL, click Add reply URL, then paste the Consumer URL you copied from the Wyebot IdP setup.
Click Save.
Next, we will configure Attributes and Claims.
Click Edit next to Attributes and Claims
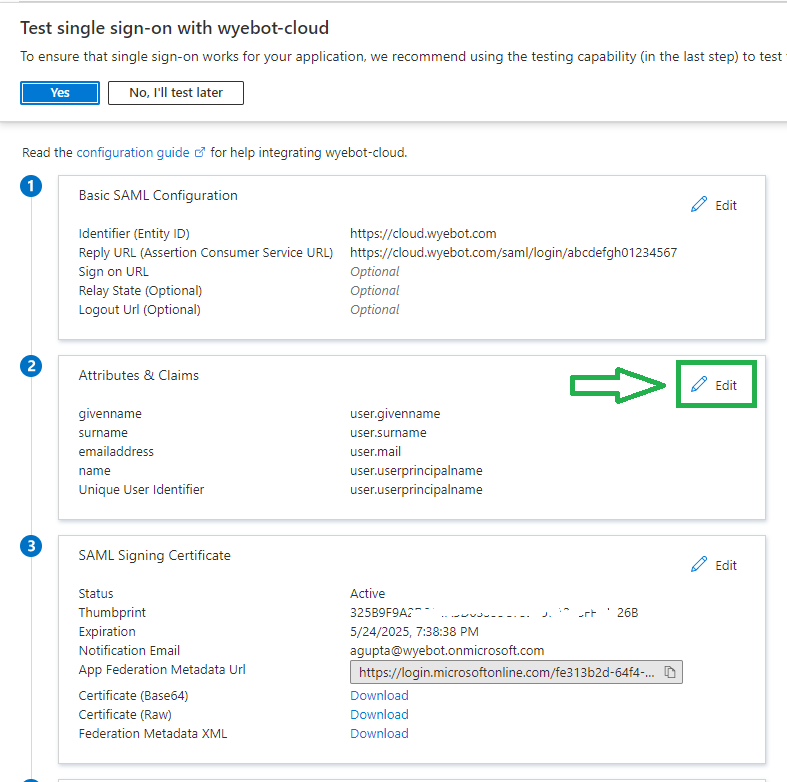
You will need to Delete all existing entries under Additional Claims.
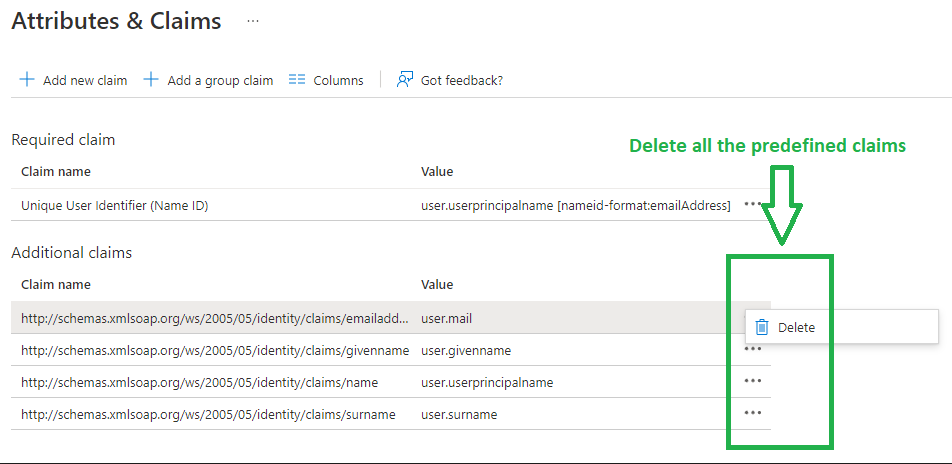
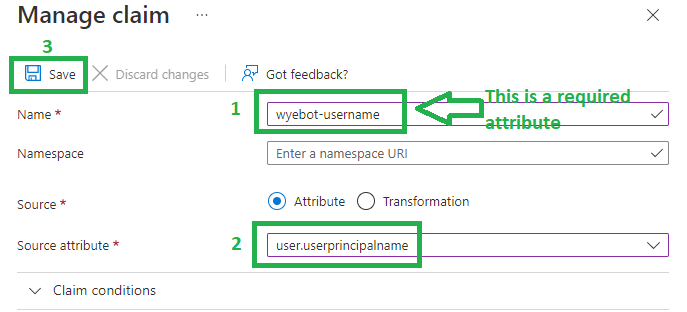
Then, click Add new claim.
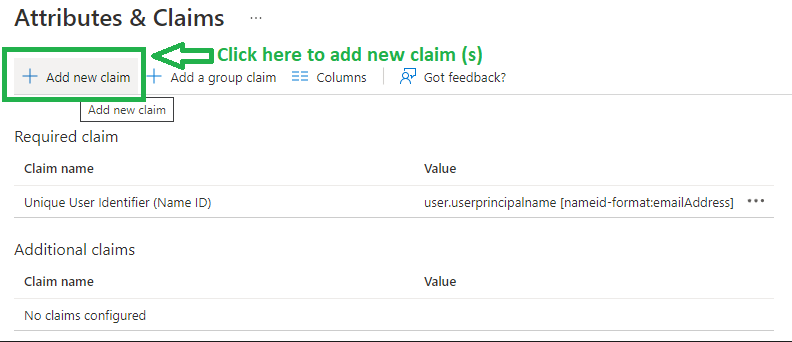
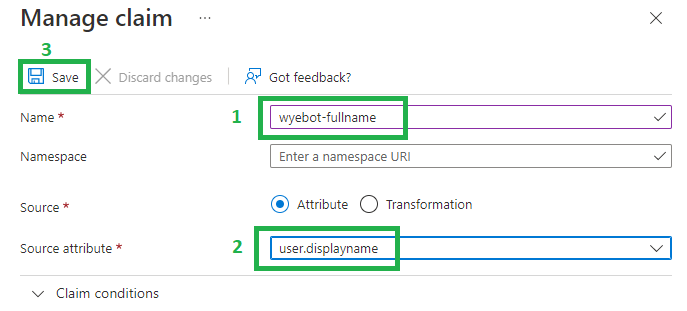
Create two new claims:
| Name | Source Attribute |
|---|---|
| wyebot-fullname | user.displayname |
| wyebot-username | user.userprincipalname |
¶ Add Azure AD Users
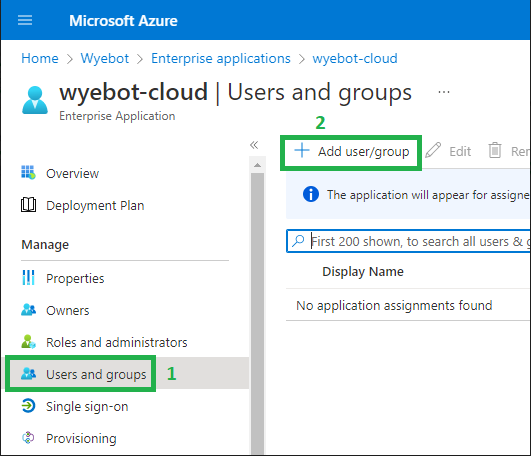
Now that you have configured the Azure console and the Wyebot dashboard, you will need to grant user access to the application.
Navigate to Users and groups, then Add user/group.
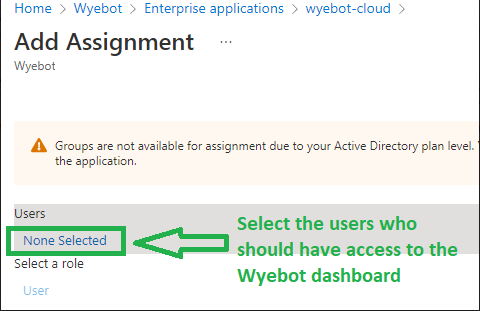
Click on None Selected, then select whichever users you wish to give access to the Wyebot dashboard.
¶ Test Connection
Now that all steps are complete, you should now be able to login using SAML authentication. The Single Sign On page of the Azure Console has a Test option which you can use to validate the setup.
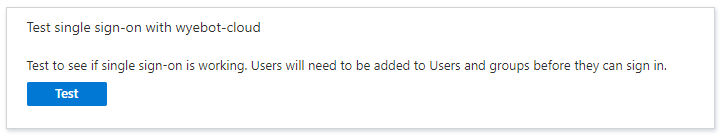
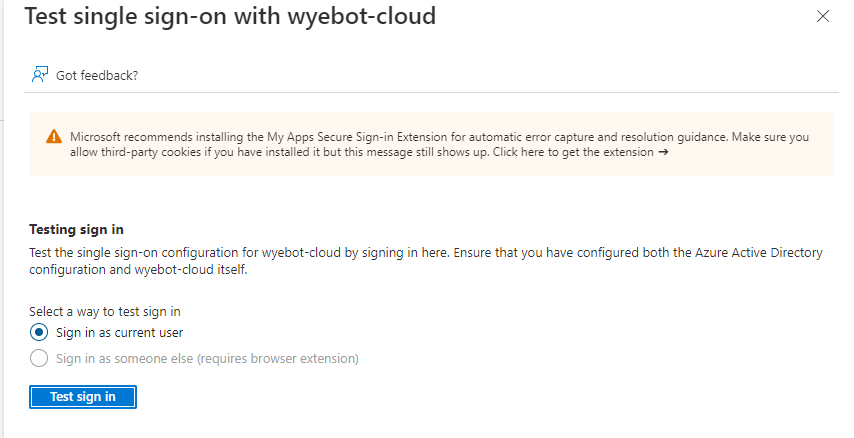
If the setup was successful, you will be redirected to your Wyebot dashboard after logging in with your Azure AD credentials.
¶ End User Access
An end user will log in to Wyebot via SAML using the Microsoft Application Portal. This can be reached at https://myapps.microsoft.com.
If they are added as a user to the Wyebot Azure Enterprise App you created, they should see it listed among your other Microsoft apps.

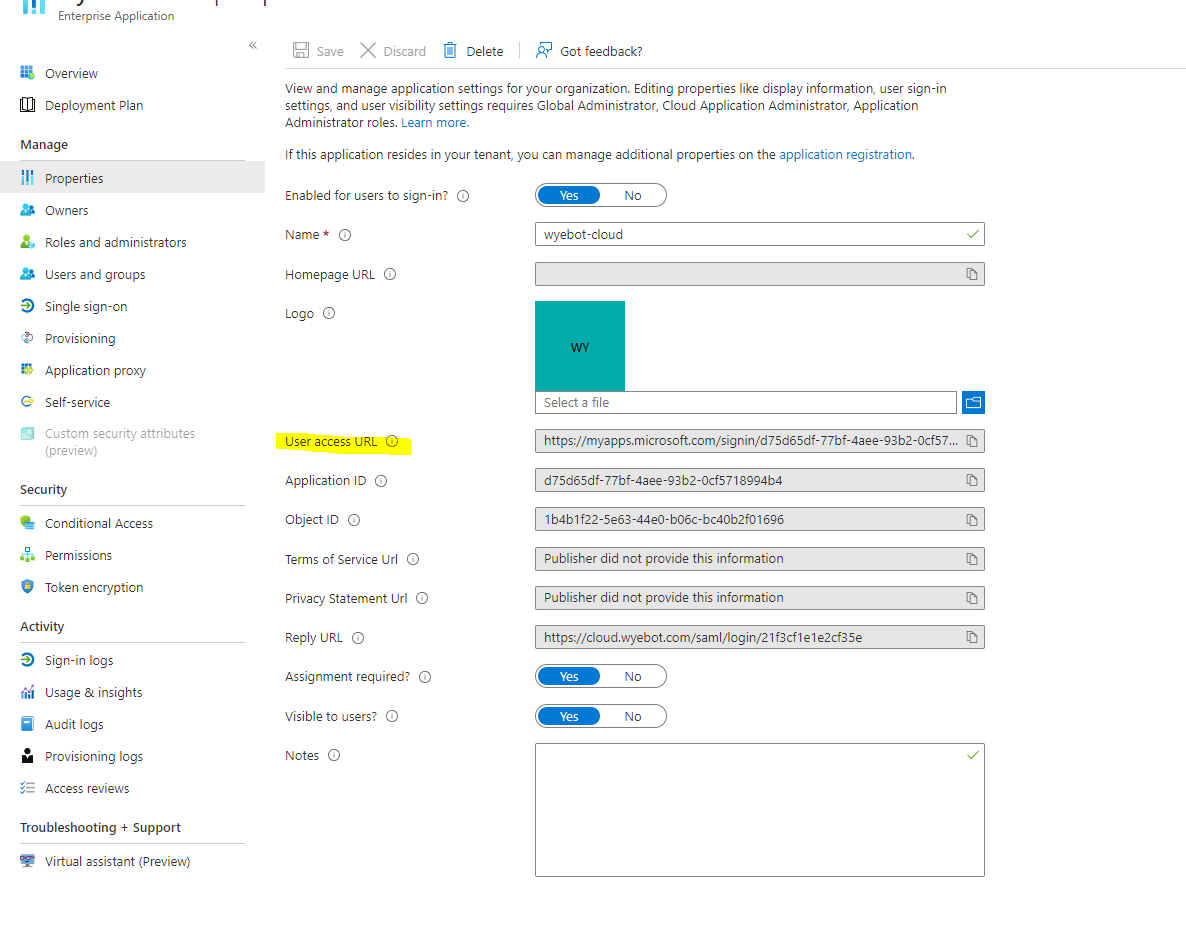
Alternatively, users may use a direct sign-on link, which can be retrieved from the Properties tab within the Wyebot Enterprise Application. Copy the User access URL shown on this page.